Featured
Table of Contents
- – What Are Vpn Tunnels And How Do They Work
- – Vpn Tunnel: What It Is And How It Works
- – What Is Vpn Split Tunneling
- – What Is Tunneling In Networking? Definition &...
- – What Is A Vpn? Types Of Vpns And How They Work
- – What Is A Vpn Tunnel, And How Does It Work?
- – Intro To Networking - Virtual Private Networ...
- – Top Vpn Protocols Explained (+ Which Ones Yo...
- – How A Vpn (Virtual Private Network) Works - ...
What Are Vpn Tunnels And How Do They Work
The strength of a tunnel depends upon the kind of tunneling procedure your VPN supplier utilizes. Some protocols are dated and may not offer information file encryption that is strong enough to hinder online snoops so it's a good concept for you to work with a VPN provider that depends on the strongest possible tunneling procedure.
That locks out numerous potential users. If you're trying to find the greatest security while online, you ought to consider purchasing a VPN service company that relies on the Open, VPN protocol. This procedure deals with all the significant os, Linux, Window, and Mac, on the mobile os of Android and i, OS.
Vpn Tunnel: What It Is And How It Works
His work has actually appeared in the Washington Post, Chicago Tribune, and Fox Business. Our offerings might not cover or safeguard versus every type of crime, scams, or threat we compose about.
The simple VPN has become significantly popular in current years, mainly due to the fact that they have the ability to bypass federal government censorship and geo-blocked websites and services. Much better still, a trustworthy VPN will allow you to do this without providing away who is doing the bypassing. In order for a VPN to do this, it develops what is known as a tunnel between you and the web.
When you link to the internet with a VPN, it creates a connection between you and the internet that surrounds your web information like a tunnel, encrypting the data packages your device sends out. While technically created by a VPN, the tunnel by itself can't be considered private unless it's accompanied with file encryption strong enough to avoid federal governments or ISPs from obstructing and reading your web activity.
What Is Vpn Split Tunneling
There are lots of types of VPN protocols that deal differing levels of security and other features. The most frequently utilized tunneling protocols in the VPN market are PPTP, L2TP/IPSec, SSTP, and Open, VPN - and the world's best VPN services ought to offer most or all of them. Let's take a more detailed take a look at them.
As a Windows-based tunneling procedure, SSTP is not offered on any other operating system, and hasn't been separately investigated for prospective backdoors constructed into the procedure. Saving the finest for last, we have Open, VPN, a relatively recent open source tunneling protocol that utilizes AES 256-bit file encryption to secure data packets.
What Is Tunneling In Networking? Definition & How It Works
A good VPN service should use you the option of a minimum of these four kinds of tunneling protocols when browsing the web. When it pertains to the finest VPN to register for there are lots of options to pick from. Obviously, if money is tight and you're not too crazy about spending anything more than you need to, attempting the best cheap VPN could be an option.
The main concern with choosing for a totally free VPN is that you generally won't get the same worth as that supplied by a paid-for competitor. What's more, if you're utilizing a VPN then one of the main considerations is going to revolve around security.
What Is A Vpn? Types Of Vpns And How They Work
Free VPNs can be a little miserly when it comes to the quantity of data you can utilize, with the operating speed regularly being less outstanding than paid-for alternatives too. If you've got a desire to stream video or are torrenting on a routine basis, this might be false economy.
Tech, Radar Pro created this content as part of a paid collaboration with Express, VPN. The contents of this article are completely independent and solely show the editorial viewpoint of Tech, Radar Pro.
What Is A Vpn Tunnel, And How Does It Work?
While it's difficult to establish by itself, Open, VPN is terrific for speed, security, and file encryption. Express, VPN users can toggle between UDP (ideal for speed) or TCP (optimum for connection reliability.)One of the more recent VPN protocols available to consumers, IKEv2 is thought about to be a lighter and more steady choice than Open, VPN.
Due to its absence of encryption and authentication features, PPTP is the fastest VPN protocol. This suggests that your internet traffic can be seen by 3rd parties. We do not advise using PPTP, and it is no longer supported on Express, VPN apps.
Intro To Networking - Virtual Private Networks & Tunneling
Table of contents It's simply plain weird to consider, isn't it? The unfortunate fact is, this is just how your connection to the internet works it's like an open window into the goings on in your house, and any nosey parker can peep through. Whether it's your Web Service Provider (ISP) looking to track and sell your information to marketers, or deceitful hackers attempting to take your personal information to sell on the dark web, it in some cases seems like the entire world has a vested interest in sleuthing on your online activity.
However, there are a number of methods to ward off prospective online snoopers, one of that includes utilizing a Virtual Private Network (VPN). In a nutshell, VPNs help you surf the web safely, independently, and without any limitations. (We have actually already waxed lyrical on the benefits of using a VPN previously, so we won't harp on again too much here).
Top Vpn Protocols Explained (+ Which Ones You Should ...
Hey, dropped connections happen in some cases, even to the very best (and most costly) VPNs. This is why most respectable VPN providers come with a seriously helpful feature an automated kill switch.
Normally, the delivery protocol runs at an equivalent or greater level in the layered model than the payload protocol.
How A Vpn (Virtual Private Network) Works - Howstuffworks
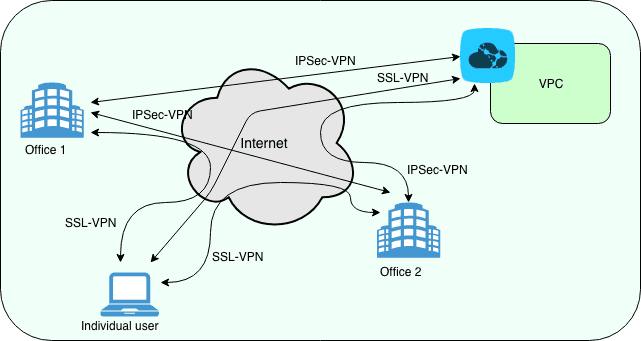
Another HTTP-based tunneling approach uses the HTTP CONNECT method/command. A client problems the HTTP CONNECT command to an HTTP proxy. The proxy then makes a TCP connection to a particular server: port, and relays data in between that server: port and the customer connection. Due to the fact that this produces a security hole, CONNECT-capable HTTP proxies frequently restrict access to the CONNECT method.
Although the SMB procedure itself includes no file encryption, the encrypted SSH channel through which it takes a trip offers security. Local and remote port forwarding with ssh carried out on the blue computer system. Once an SSH connection has been developed, the tunnel begins with SSH listening to a port on the remote or regional host.
Table of Contents
- – What Are Vpn Tunnels And How Do They Work
- – Vpn Tunnel: What It Is And How It Works
- – What Is Vpn Split Tunneling
- – What Is Tunneling In Networking? Definition &...
- – What Is A Vpn? Types Of Vpns And How They Work
- – What Is A Vpn Tunnel, And How Does It Work?
- – Intro To Networking - Virtual Private Networ...
- – Top Vpn Protocols Explained (+ Which Ones Yo...
- – How A Vpn (Virtual Private Network) Works - ...
Latest Posts
How To Choose The Best Vpn For Your Start-up
Best Virtual Private Networks Reviews 2023
Best Vpns Of August 2023
More
Latest Posts
How To Choose The Best Vpn For Your Start-up
Best Virtual Private Networks Reviews 2023
Best Vpns Of August 2023